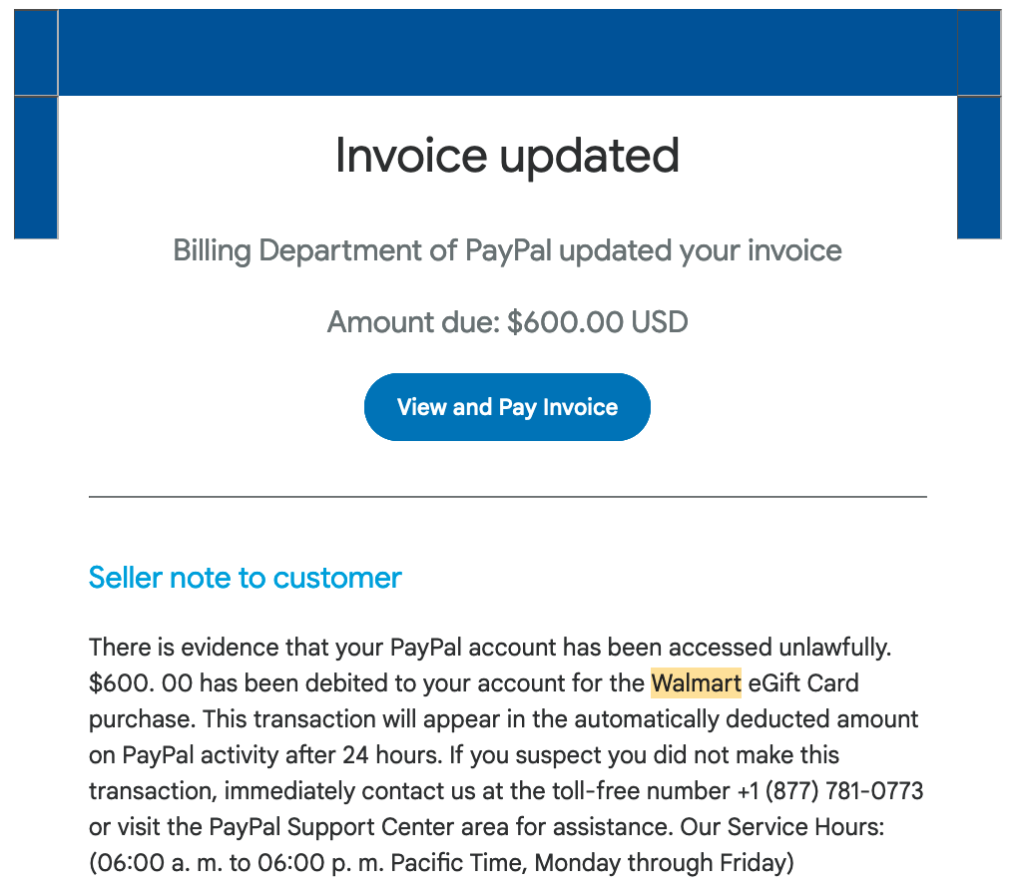
So, a few days ago I got one of the most sophisticated phising scam messages I’ve ever received. Message:
Bluehost.com
2:46 PM (5 hours ago)
to me
Hello, LAWRENCE PERSON
We are contacting you today because we have disabled your outbound email services temporarily. The reason for this is because you've got a forum that spammers were subscribing to to get messages sent out. They used a spam trap email address that actually resulted in our mail server getting blacklisted.
We need you to add protection to it so it isn't being exploited in the future. You will need to contact us and let us know this has been resolved for us to restore your email services.
For protection, we ask that you require an account to subscribe to topic notifications if you haven't already. We also ask that you add protection to your sign-up page so that spammers cannot automate it. You can do this by using a captcha or something similar to that.
To activate your account, please visit our BlueHost account reactivation center. Use the link below:
http://my.bluehost.com.313e7d092611f0c58251064957ca6b4c.
cajunhomeservices.com/account/58961/reactivation.html
Thank you,
BlueHost.com Terms of Service Compliance
http://www.bluehost.com
For support go to http://helpdesk.bluehost.com/
Toll-Free: (888) 401-4678
Note the relatively good English and the fairly sophisticated “You have a technical spam problem” hook. The all caps name and the fact I don’t have any “forums” is the only giveaway, besides an examination of the actual link provided, that it’s not kosher.
Note that the link actually points to “cajunhomeservices.com”.
Raw source:
Delivered-To: l********@gmail.com
Received: by 2002:ac2:518f:0:0:0:0:0 with SMTP id u15csp11449403lfi;
Thu, 14 Nov 2019 12:46:12 -0800 (PST)
X-Google-Smtp-Source: APXvYqzeSBr4ElY5I4kaRQJbufydJ32F7GyXgzop2lpZkta8d7s7
RkuuytltMNPtM4up1GCCTCwr
X-Received: by 2002:aca:52c2:: with SMTP id g185mr5152898oib.45.1573764372228;
Thu, 14 Nov 2019 12:46:12 -0800 (PST)
ARC-Seal: i=1; a=rsa-sha256; t=1573764372; cv=none;
d=google.com; s=arc-20160816;
b=sPXkzlz9bAXMXM5E2CaRKG6d6ybRdOxTCNcjZNm5e5kMRkr4KWL
2xq4PjgaGnn3KIYbVmgahiHv7Trl3QgGFzbryJNeeX5VNhxK/
cSIumeiQnlB3aNUV/0qfNY1Cu6szqcMn890SG6r/
7Nvq3XWQ0kGiPBdTAELDw8QS8bpgIPrSHeKPJ669ifn50yKL7KybJ
PnrlQrJe8rWDPDAag1kkJpPhEWIzhWzETQpMW65pUVsuO4SoleoVo
MRHR4WWZ3x4UgY+I7+s58RjcHDx+uSS5UYboFJd6n+ksMZQUNI9rq
MmUYIdq3GLvXAekXAbIXyzUYo+24K2Z0iusbAJo
CQGA==
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816;
h=content-transfer-encoding:mime-version:from:to:subject:message-id
:date;
bh=sZf91ll1kaMuGiSLWB5C0DKuw/3r72M1cUA1iJqiuLw=;
b=b5CGhK96w1NqMgkAhr04RJAsjO9YKteraSIV/tvZoFeuEGUhGlHF
nxu8r3KLVTb5fNbAJXyxbLxSy+vxpXeZXhMLcS+OApLDERBmuJ9Pm
VH9TTxayaPbpqTHvyKgCGRr6JG4aM12/7CdqWxy3aH5hRvKwYg8Y35
xZZ0jQgnngrEXsx9glAX3S78XsCGS27BCKzoB/qA7c4245rT7rEXf3
y6uRyZSe6Kc9FaYotV7j5VpjhVr0c+qcf7iJUFtdjLSkYW/BlY2baA
jGq3WixP5g3y9fYZ8X636dLLFcu7PKpKsb324VRcRgKJONc356J7x0
K4I+pEk3oLxlMa8T3
/RLw==
ARC-Authentication-Results: i=1; mx.google.com;
spf=fail (google.com: domain of support@bluehost.com does not designate 192.185.143.39 as permitted sender) smtp.mailfrom=support@bluehost.com;
dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=bluehost.com
Return-Path:
Received: from gateway31.websitewelcome.com (gateway31.websitewelcome.com. [192.185.143.39])
by mx.google.com with ESMTPS id f84si4367574oig.42.2019.11.14.12.46.11
for
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Thu, 14 Nov 2019 12:46:12 -0800 (PST)
Received-SPF: fail (google.com: domain of support@bluehost.com does not designate 192.185.143.39 as permitted sender) client-ip=192.185.143.39;
Authentication-Results: mx.google.com;
spf=fail (google.com: domain of support@bluehost.com does not designate 192.185.143.39 as permitted sender) smtp.mailfrom=support@bluehost.com;
dmarc=fail (p=NONE sp=NONE dis=NONE) header.from=bluehost.com
Received: from cm13.websitewelcome.com (cm13.websitewelcome.com [100.42.49.6]) by gateway31.websitewelcome.com (Postfix) with ESMTP id BD99FD53F0 for ; Thu, 14 Nov 2019 14:46:11 -0600 (CST)
Received: from box2082.bluehost.com ([50.87.249.228]) by cmsmtp with SMTP id VM0Ji8N6s3Qi0VM0JiRiqR; Thu, 14 Nov 2019 14:46:11 -0600
X-Authority-Reason: ss=1
Received: from [162.248.225.8] (port=55837 helo=support) by box2082.bluehost.com with esmtpsa (TLSv1.2:ECDHE-RSA-AES256-GCM-SHA384:256) (Exim 4.92) (envelope-from ) id 1iVM0J-003aX1-95 for l*******@gmail.com; Thu, 14 Nov 2019 13:46:11 -0700
Date: Thu, 14 Nov 2019 15:48:38 -0500
Message-ID: <1332064982.webi20191114154838@bluehost.com>
Subject: Disabled your outbound email services temporarily
To: l********@gmail.com
From: "Bluehost.com"
X-Priority: 4 (Low)
Mime-Version: 1.0
X-Mailer: Php_libMail_v_2.11(webi.ru)
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: base64
X-AntiAbuse: This header was added to track abuse, please include it with any abuse report
X-AntiAbuse: Primary Hostname - box2082.bluehost.com
X-AntiAbuse: Original Domain - gmail.com
X-AntiAbuse: Originator/Caller UID/GID - [47 12] / [47 12]
X-AntiAbuse: Sender Address Domain - bluehost.com
X-BWhitelist: no
X-Source-IP: 162.248.225.8
X-Source-L: No
X-Exim-ID: 1iVM0J-003aX1-95
X-Source:
X-Source-Args:
X-Source-Dir:
X-Source-Sender: (support) [162.248.225.8]:55837
X-Source-Auth: bh_1572749987@sandiegoslushkin.com
X-Email-Count: 9
X-Source-Cap: c2FuZGlmbjk7c2FuZGlmbjk7Ym94MjA4Mi5ibHVlaG9zdC5jb20=
X-Local-Domain: no
SGVsbG8sIExBV1JFTkNFIFBFUlNPTg0KIA0KV2UgYXJlIGNvbnRhY3RpbmcgeW91IHRvZGF5IGJl
Y2F1c2Ugd2UgaGF2ZSBkaXNhYmxlZCB5b3VyIG91dGJvdW5kIGVtYWlsIHNlcnZpY2VzIHRlbXBv
cmFyaWx5LiBUaGUgcmVhc29uIGZvciB0aGlzIGlzIGJlY2F1c2UgeW91J3ZlIGdvdCBhIGZvcnVt
IHRoYXQgc3BhbW1lcnMgd2VyZSBzdWJzY3JpYmluZyB0byB0byBnZXQgbWVzc2FnZXMgc2VudCBv
dXQuIFRoZXkgdXNlZCBhIHNwYW0gdHJhcCBlbWFpbCBhZGRyZXNzIHRoYXQgYWN0dWFsbHkgcmVz
dWx0ZWQgaW4gb3VyIG1haWwgc2VydmVyIGdldHRpbmcgYmxhY2tsaXN0ZWQuDQoNCldlIG5lZWQg
eW91IHRvIGFkZCBwcm90ZWN0aW9uIHRvIGl0IHNvIGl0IGlzbid0IGJlaW5nIGV4cGxvaXRlZCBp
biB0aGUgZnV0dXJlLiBZb3Ugd2lsbCBuZWVkIHRvIGNvbnRhY3QgdXMgYW5kIGxldCB1cyBrbm93
IHRoaXMgaGFzIGJlZW4gcmVzb2x2ZWQgZm9yIHVzIHRvIHJlc3RvcmUgeW91ciBlbWFpbCBzZXJ2
aWNlcy4NCg0KRm9yIHByb3RlY3Rpb24sIHdlIGFzayB0aGF0IHlvdSByZXF1aXJlIGFuIGFjY291
bnQgdG8gc3Vic2NyaWJlIHRvIHRvcGljIG5vdGlmaWNhdGlvbnMgaWYgeW91IGhhdmVuJ3QgYWxy
ZWFkeS4gV2UgYWxzbyBhc2sgdGhhdCB5b3UgYWRkIHByb3RlY3Rpb24gdG8geW91ciBzaWduLXVw
IHBhZ2Ugc28gdGhhdCBzcGFtbWVycyBjYW5ub3QgYXV0b21hdGUgaXQuIFlvdSBjYW4gZG8gdGhp
cyBieSB1c2luZyBhIGNhcHRjaGEgb3Igc29tZXRoaW5nIHNpbWlsYXIgdG8gdGhhdC4NCg0KVG8g
YWN0aXZhdGUgeW91ciBhY2NvdW50LCBwbGVhc2UgdmlzaXQgb3VyIEJsdWVIb3N0IGFjY291bnQg
cmVhY3RpdmF0aW9uIGNlbnRlci4gVXNlIHRoZSBsaW5rIGJlbG93Og0KaHR0cDovL215LmJsdWVo
b3N0LmNvbS4zMTNlN2QwOTI2MTFmMGM1ODI1MTA2NDk1N2NhNmI0Yy5jYWp1bmhvbWVzZXJ2aWNl
cy5jb20vYWNjb3VudC81ODk2MS9yZWFjdGl2YXRpb24uaHRtbA0KDQogDQpUaGFuayB5b3UsIA0K
Qmx1ZUhvc3QuY29tIFRlcm1zIG9mIFNlcnZpY2UgQ29tcGxpYW5jZQ0KaHR0cDovL3d3dy5ibHVl
aG9zdC5jb20NCkZvciBzdXBwb3J0IGdvIHRvIGh0dHA6Ly9oZWxwZGVzay5ibHVlaG9zdC5jb20v
DQpUb2xsLUZyZWU6ICg4ODgpIDQwMS00Njc4
(Note: Line breaks added on ARC lines.)
Note the authentication fails in the raw source of the message.
Let’s do a whois for cajunhomeservices.com:
Domain Name: CAJUNHOMESERVICES.COM
Registry Domain ID: 1987624026_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.fastdomain.com
Registrar URL: http://www.fastdomain.com
Updated Date: 2018-12-16T00:21:49Z
Creation Date: 2015-12-16T00:22:33Z
Registry Expiry Date: 2019-12-16T00:22:33Z
Registrar: FastDomain Inc.
Registrar IANA ID: 1154
Registrar Abuse Contact Email:
Registrar Abuse Contact Phone:
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: NS1.BLUEHOST.COM
Name Server: NS2.BLUEHOST.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2019-11-15T02:46:01Z <<<
The interesting thing here is that cajunhomeservices.com is actually registered to bluehost.com. I launched a chat window with technical support (offshore, it seemed like), and they promised to alert the proper security staff.
Lesson: If you receive a message alerting you to some sort of online fraud, never click any link in the message. If it's a domain or service you use, go there by your saved bookmark or by typing the domain URL directly into your browser.
Eternal vigilance is the price of IT security...