Merry Christmas, everyone! To celebrate, enjoy this video of Christmas package thieves getting bombed:
Glitter Bomb 4.0
December 25th, 2021What 12th Man?
December 23rd, 2021Texas A&M’s football team has withdrawn from the Gator Bowl following a bout of Flu Manchu.
News broke on Tuesday that A&M’s football team had not practiced since last Saturday as a number of athletes had tested positive prior to the Aggies hitting the practice field on Sunday and then again during the next two days. The team was supposed to be released to go home on Tuesday until Dec. 26 when players were to make their way to Jacksonville for final bowl preparations. People both within the program and the highest levels of the administration were pessimistic as early as Tuesday night due to practical considerations arising from numbers via NCAA protocols that the game would take place.
The Aggies were already down quite a few players going into bowl game workouts last week given their status due to injuries and opt outs even before news of possible problems with COVID tests had emerged. There are as many as ten upperclassmen who are draft eligible who could or already have opted out of the game. In addition, two more (Zach Calzada and Dreyden Norwood) have entered the NCAA transfer portal since the regular season ended. Finally, by our count, there are as many as 12 players who are done for the season and won’t play in the game due to injury. Those items push the Aggies down towards approximately 60 scholarship players being available for the game including just one quarterback in Haynes King (who missed most of the season himself due to a broken ankle and has just returned to workouts).
Wait, 60 players? That’s seven more than an NFL roster. You need 11 players each side, for a total of 22. (And prior to 1941, the same players played both offense and defense.) You’ve got enough to play, even if a few players have to learn new positions in a hurry. It’s the postseason, the only postseason your team gets this year, and you’re wimping out.
Also note: “Scholarship” players. Whatever happened to the much-vaunted “12th Man” tradition at A&M, about to turn a century old? One of the features of the 12th Man was a willingness to play walk-ons. A bet dozens (if not hundreds) of ex-high school football playing Aggies would be happy to volunteer to join the football team in their hour of need. And I bet the NCAA would approve it.
But no, we can’t have that. Better to cancel it because someone might get an ouchie.
Evidently the Aggies of 2021 just aren’t made of the stern stuff of the Aggies of 1922. Or even 1983.
Texas and Florida Added More Than Half The Nation’s New Jobs In November
December 18th, 2021You may have heard that the America added an anemic 210,000 jobs in November, which was (as has become standard in the Biden era) much less than “experts” predicted.
The news wasn’t great, but Texas did well:
Employment in Texas has reached nearly 13 million non-agricultural jobs, eclipsing the pre-pandemic high set in February of 2020.
From October, the unemployment rate dropped 0.2 percent with the addition of 75,100 jobs. Since November of last year, 698,700 jobs have been added to the rolls.
“By reaching nearly 13 million jobs last month, Texas has surpassed our pre-pandemic employment levels — a remarkable achievement and testament to our welcoming business climate and strong workforce,” Governor Greg Abbott said in a release.
According to the Texas Workforce Commission (TWC), Amarillo continues to post the lowest unemployment rate in the state at 3.1 percent. Austin-Round Rock follows closely behind at 3.2 percent.
Also crowing about adding jobs: Florida governor Ron DeSantis, whose state added 50,000 jobs:
Florida added over 50,000 new jobs in the month of November, a much faster rate than the nation, which added 210,000 jobs in November. pic.twitter.com/7LOG5ZipAY
— Ron DeSantis (@GovRonDeSantis) December 17, 2021
75,100 + 50,000 = 125,100. So just shy 60% of jobs added in November came from two states known for low taxes, light regulation and general economic freedom.
(If you dig further into the statistics, the lesson is a bit less clear cut, with California (45,700), New Jersey (25,800) and New York (23,600) ranking 3-5 for most jobs added.)
According to census data, Texas and California have a combined population of 50,683,692, while the U.S. has a census-estimated population of 328,239,523. (Both those numbers have undoubtedly gone up a bit since census data was released in July.) Which means that two states with less than 1/6th the total population of the U.S. accounted for more than 60% of job growth.
Why, it’s almost as if red states run by Republican governors are better at creating jobs than blue states run by Democratic governors…
Log4J and Internet Castles Made of Sand
December 16th, 2021If you work outside of a tech company, chances are you’ve spent this week primarily concerned with getting ready for Christmas. If you work inside a tech company, there’s a significant chance your company spent much of this week patching a critical vulnerability in an open source Java logging library called Log4J.
Here’s a non-technical explanation of the problem:
It’s a vulnerability that was discovered in a piece of free, open source software called log4j. This software is used by thousands of websites and applications, to perform mundane functions most people don’t think about, such as logging information for use by that website’s developers, for debugging and other purposes.
Every web application needs functionality like this, and as a result, the use of log4j is ubiquitous worldwide. Unfortunately, it turns out log4j has a previously undiscovered security vulnerability where data sent to it through that website — if it contains a special sequence of characters — results in log4j automatically fetching additional software from an external website and running it. If a cyberattacker exploits this, they can make the server that is running log4j run any software they want — including software that can completely take over that server. This is known as a Remote Code Execution (RCE) attack.
To use a technical phrase, this is Really Bad.

The net result is that, left unaddressed, cyberattackers right now can completely take over thousands of websites and online applications, allowing them to steal money, data, and access. The security community has been completely focused on this vulnerability for the past two days, and updating servers running log4j as quickly as possible to protect against this vulnerability.
The good news is that mitigations are relatively easy to implement. The bad news is that left unmitigated, the vulnerability is extremely easy to exploit. iCloud, Minecraft, Baidu, and many other sites have been confirmed to be vulnerable so far, and you’ll likely hear more about many other sites being vulnerable in the coming days.
And those companies are just the tip of the iceberg. LAMP stacks (Linux, Apache, MySQL, and PHP) are used as the technological underpinnings for a wide variety of web applications of all sizes. (It’s not universal, as NGINX has taken over as a market leader from Apache, and there are still a few all-Microsoft houses that use IIS, and neither of them have the vulnerability.)
Open Source has been a revolutionary invention because it provides rapid development by armies of distributed developers, and Linus’s Law states that “with enough eyes, all bugs are shallow.” But there are tens of thousands of Open Source components out there running critical infrastructure that haven’t had nearly as many eyes on the code as the Linux kernel. It’s simply the nature of the beast. XKCD had a cartoon for this occasion:
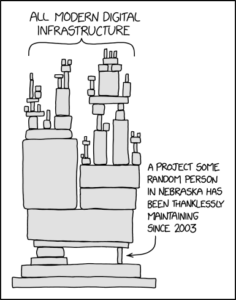
Internet applications gain usefulness from widespread adoption and the number of other components they tie into and support. You know what creates new vulnerabilities? A larger user base and the number of other components they tie into and support, which creates more attack surfaces for malicious actors to exploit.
The flaw isn’t the fault of Random Guy in Nebraska, the fault is the company adopting software that they can’t possibly test for all the use-cases they’re going to use it for. Surprise! Just about every high tech company in the world is in the same boat. Pretty much everyone uses a wide panoply of open source tools for their Internet applications, and no one can test all the permutations of how each component might be put to use.
You can’t eliminate the risk, you can only minimize and mitigate it. You can use containerization strategies (Docker, Kubernetes, Container D, etc.) to minimize attack surfaces and limit contagion. You can run all your code through security scanning tools on your CI/CD platform of choice. You can do constant testing and keep rolling backups of everything to limit risk and speed recovery. (You can also train your employees not to click on random email links without verifying the sender is who they say they are, and not to give any any account information or passwords over the phone, and train them enough so that the lessons stick, even though phising and human engineering weren’t factors in the Log4J vulnerability.)
But there still a good chance that the platform you’re using today is different than the platform you’ll be using ten years from now, and you’ll have to go through the same learning lessons discovering new vulnerabilities for the new platform all over again.
Castles made of sand all fall into the sea eventually…


